Article How to Implement an IT Security Plan in Wealth Management
By Insight Editor / 1 Jun 2018

The cost of cybercriminal activity steadily grew between 2013 and 2015, and 2016 brought a sharp rise in the amount of money businesses spend on recovering from cyber attacks.
In a study of 254 companies across 15 industries, Accenture learned that businesses spent on average $11.7 million a year on overcoming cybercrime in 2017.
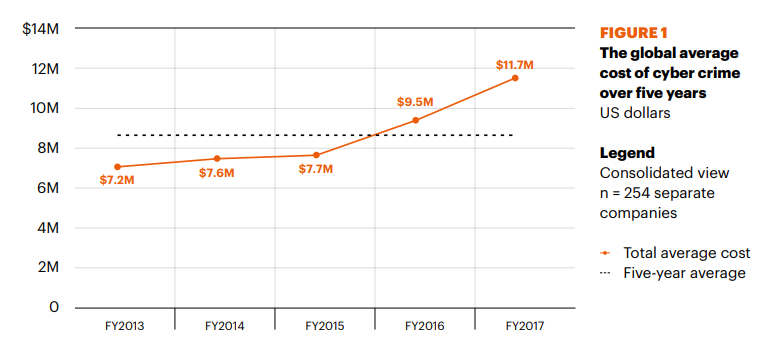
The financial services, utilities and energy, and aerospace and defence industries were hit hardest. Each sector spent well above the average cost of curbing cybercrime.
However, the financial services industry was the worst hit — firms in this industry spent on average 70% more than their non-finance counterparts.
It’s true that legacy applications — and old IT systems in general — are at particular risk of being vulnerable to today’s cyber threats. However, even those embarking on the path of digital transformation through the adoption of new technologies are not immune.
Rather, as we adopt new systems – such as artificial intelligence, internet-of-things and machine learning – to gain efficiencies and achieve new outcomes, we’ll also be exposed to new kinds of security threats.
And, IT technologies aren't the only area of risk. Threats can also manifest in the form of user behavior and organizational processes.
Be it an upgrade of your existing IT infrastructure or a plan for digital transformation, it’s vital that you rely on best IT security practices when defining your technology roadmap.
How People Affect IT Data Security Plans
People are often the weakest layer in IT security, even if they work within a technically strong security system. For example, human error or malicious intent can result in the exposure of your company’s passwords, confidential information, data, and other assets.
How are People ‘The Weakest Link?’
You might already be familiar with "phishing attacks" in which emails masked as messages from your bank, utility provider, or the government trap unwitting victims into clicking and, in some cases, providing their usernames, passwords, or even social security numbers.
The human factor is a constant in both personal and professional matters. But in the latter, a compromised login will not only affect the user, but the business as well. Thus, human error is a major vulnerability for organizations handling sensitive data.
Malicious Insiders
While most human security errors are unintentional, some can be malicious. Think of a disgruntled or a former employee who is looking to damage your business by stealing competitive secrets.
In fact, it need not be limited to just damaging the company; the financial services industry (e.g. investors and wealth management firms) are at risk of internal fraudulent activity too.
User IT Education & Training
When it comes to human error, the best starting point is to ensure that your staff are thoroughly educated and trained in terms of countering phishing attacks.
The simplest lessons, such as how to differentiate between a real message and a fraudulent one, cover a lot of ground in a short amount of time.
In terms of mitigating malicious activity from within, you’ll need to fine-tune your IT security processes and technology.
IT Cyber Threat Security Best Practices & Processes
Your organizational processes are the means through which you can respond to an IT security incident, including a breach.
In fact, it’s not just a best practice at this stage, but something that’s required as part of regulatory compliance. The leading example of this is the European Union’s (EU) General Data Protection Regulation (GDPR).
Essential Elements
In terms of incorporating processes for your IT security planning, consider these:
- IT Security Leadership: It’s imperative that your organization maintains a clear-cut IT security chain-of-command.
Not only does your workforce need to be security-conscious, but there must be clear lines of accountability and responsibility for all security matters. - Incident Response and Management: Should an incident occur with your IT security system (especially a breach), you must have strong response processes.
This should include a strong communications plan. For example, the GDPR requires notification of breaches within 72 hours.
In addition, your plan for protecting and recovering affected assets should be tested and ready for immediate deployment. - Connect with External Stakeholders: It’s a must to have business privacy, security, and data-collection agreements (e.g. privacy policy) built with any of your third-party vendors.
The above would seem like common sense, but in a recently published study, Accenture found that on average only 30-40% of businesses actually have strong IT security processes.
It’s not surprising then that EY (Ernst & Young) outlined that an incredible 35 million cyber attacks took place on enterprises and large organizations in 2016.
In the financial services industry, there’s little room for recovery after a cyber attack, especially when client data is involved. The loss of reputation could essentially halt your future prospects for growth and revenue generation.
Thus, the technology side of your IT security best practices must position cyber resilience, a strategy for preventing cyber attacks from doing major damage to your business, at the forefront.
IT Data Security Technology
Before proceeding with an IT security technology solution, you should conduct an audit of your existing system to identify your cyber threats and vulnerabilities. This is an essential cybersecurity best practice.
Cloud Data Security and Privacy
Current applications draw on the cloud for many essential functions -- including the collection, processing, and hosting of client data that must be protected.
Given that threats posed to data are both digital and physical, you’ll need a robust and credible hosting solution. This can be costly, as it depends on experienced talent, tight adherence to security and compliance standards, and routine updates.
This is where a managed IT service provider — especially one with tier-one partnerships with the cloud industry’s leading vendors — goes a long way in achieving the necessary cyber security and compliance requirements in a cost-effective manner.
Device and User Management
Proper device and user management elements will help guard your IT system against human error and malicious insider activity. For example, you can swiftly respond to a lost device or outgoing employees with remote data-wiping.
Likewise, enforcing user policies at various levels of your system along with layered access controls will ensure that your most sensitive assets (such as client data) are only accessible to a few trusted individuals.
You can bypass the complicated and costly process of internally building a robust device and user management system by working with a managed IT partner with the required security credentials.
Deploying Cyber Data Security Best Practices for Your Applications
Your applications are essential to driving business operations and engaging with customers. However, if these apps are not secure, then they’re vulnerabilities that threaten to expose your system assets to cybercriminals.
A policy of cyber resilience dictates that you work to prevent these vulnerabilities from materializing into actual cyber attacks.
If you lack the internal IT resources to properly secure your current and future applications, an external developer with the requisite staff, industry expertise and credibility can quickly close your security gaps.
Granted, incorporating cybersecurity best practices into your IT security system’s business plan will result in comparatively high costs. However, it is a necessary expense.
Furthermore, by safeguarding your IT system today you’re protecting yourself from future – and much greater – costs down the line by avoiding regulatory penalties and the costs of recovering from cyber attacks.
Consider reaching out to Insight for a free consultation. We can discuss how our tier-one partnerships will enable you to readily incorporate financial IT solutions, insurance IT solutions, or wealth management solutions in your IT roadmap.
Ensuring You Aren’t Vulnerable To Cyber Threats
Data Security
The Verizon 2016 Data Breach Investigations Report found that 63% of breaches involve weak, default, or stolen passwords.
The overall result of the survey found that basic defenses were lacking, and that your entire staff needs to be vigilant, not just your IT team.
Look Out For Breaches in Data Security.
The report found over 100,000 reported security incidents, of which 3,141 were confirmed data breaches. In 93% of those confirmed cases, it took attackers minutes or less to compromise systems, and in 28% of them, data extraction occurred within minutes.
It doesn’t take a determined hacker very long to get what they want once they’re in.
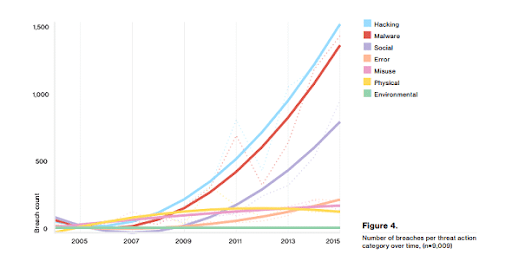
And if you think these breaches are restricted to retail environments to steal credit card information, you’re wrong. The public services sector experienced 47,237 incidences of security attacks in 2015, with finance experiencing 1,368, and the healthcare sector experiencing 166.
Data Phishing Should Be A Top Data Security Concern:
Spear-phishing often takes the form of emails from a fraudulent source that masks itself as a trusted party, with the goal of fooling the end-user into clicking on a virus or giving up login information.
Both approaches can cause major problems for your business, including installing malware on the end user’s PC, which can then spread quickly through your organization’s network.
Alternatively, the hacker might trick the user into giving their username and password to their email or another application. This can give the hacker an opening into your system.
While the majority of people are becoming more aware of these types of malicious emails, a total of 13% of these emails were opened with a relatively high click-through rate — accounting for a total of 916 incidents of a confirmed data breach.
How You Can Improve Your Data Security:
Provide training on how your staff is to react when they suspect an email is suspicious.
Include the basics of email delivery such as:
- Don’t auto-open emails one after the other. Carefully read subject lines and view the sender before opening.
- If an email seems suspicious, train your staff to ask questions and immediately inform your IT team.
- Ensure that your anti-malware and anti-spam filters are keeping malicious emails from reaching employee inboxes.
- Regularly inform your staff about phishing scams. Including this information in internal memos or newsletters helps your team remain vigilant.
- Reach out to your software management services provider for further consultation or to discuss data security options
Avoiding Misuse Of Data
As you may know, Edward Snowden orchestrated one of the biggest information leaks ever due to his position as systems engineer and administrator at the US National Security Agency (NSA). He revealed global intelligence data somewhere to the tune of 50,000 to 200,000 documents.
According to the Verizon DBIR, 88% of insider misuse was a result of an abuse of privilege. Providing access rights to all employees for everything within your company can lead to disgruntled staff or opportunistic employees taking advantage of their access.
It’s not always your employees who are the ones perpetrating these attacks, however; they could be the target of a carefully orchestrated hack simply because of their access controls. Ensuring these gatekeepers or super users follow stricter password protocols can help with this potential data security vulnerability.
What you can do:
Track and analyze the access of all users, including super users, through log management that tracks human behaviors, including:
- What time of day were accounts accessed?
- What behavioral patterns are being followed?
- Has one of your end-users randomly starting using the command line to search through your network?
Keeping an eye on activity can identify drastic changes that clue your IT team into whether an employee’s account has been hacked, or if they are downloading sensitive information.
Deploy Data Security Best Practices to Avoid Losing Information
Your employees are given access to your company information, whether from a personal device or a company-owned one.
If protocols aren’t established to ensure that you can quickly and easily wipe a lost device, that access could land in the wrong hands.
Lost or stolen assets only account for 15% of incidents, but if proper password protections and access privileges aren’t established on the device, the “finder” of that laptop or phone could expose company data simply out of opportunity.
What you can do:
Establish secure bring-your-own-device (BYOD) policies that are aimed at establishing access controls, such as passwords and multi-factor authentication, and make sure that your IT team can remotely wipe the device of any and all sensitive information.
Ensure that your team understands the importance of immediately notifying IT if their device has been lost. It is still better to enforce data security processes than to issue punishment over lost devices. Your staff shouldn’t be afraid to admit their loss.
If you’re still concerned that these measures aren’t enough or that your system may have gaps that a hacker could slip through, get in touch with our team at Insight.
We offer the latest security software and customizable security assessments to ensure that your network, devices, apps and servers are safe and secure.
Only through proactive procedures can you prevent your organization from becoming the next cyber victim.
Internet Security Solutions for Cyber Threats
Enforcing corporate web traffic security policies is not just about controlling the websites your users visit. In fact, many of the new threat vectors these days target web browsers.
Having a web security appliance, such as Cisco IronPort, to control user browsing activities can help increase productivity but can also defend against threats targeting browsers.
The Cisco IronPort S series of web security appliances are designed to apply company policies to web traffic. The S series has a number of advanced features that allow deep visibility into web traffic to ensure that company policies are implemented.
URL Categorization
IronPort uses the traditional method of categorizing URLs into a large number of groups that allow policies to be applied based on the categories of the URL.
However, due to the changing nature of the Internet, it is impossible to categorize all URLs, so IronPort can also use the Cisco Senderbase network to categorize URLs based on traffic collected from around the globe.
The Senderbase network first appeared on the IronPort Email Security Appliances to assign a reputation value to an email source, allowing an administrator to control what email was allowed or dropped.
This value assigned to a URL is called the Web Reputation Score or WBRS.
The Web Reputation Score (WBRS)
The WBRS is a value from -10 to 10 and protects against URL-based malware, a growing threat.
By default, a score of -10 to -6 is blocked right away, as this score indicates that the site is more likely to contain malware. An example may be a site which is a typo of a popular site.
A score of -5.9 to 5.9 will be scanned by the IronPort Dynamic Vectoring and Streaming (DVS) engine, which inspects for anomalies in web traffic from both the client and the server.
DVS can inspect the user agent for suspicious activity, which may indicate that the client is infected with malware. It’ll also scan with Webroot, McAfee and Sophos anti-malware utilities to ensure that the client is not compromised.
Scores of 6.0 to 10 are allowed with no scanning. These scores indicate a trusted web site with an established reputation which is very unlikely to be hosting malware.
Application Visibility & Control
Besides the URL categorization and Web reputation filtering, the IronPort has another feature called Application Visibility & Control.
A large number of popular websites may have a useful business function but also include applications that may not be approved.
An example of this is Facebook. It can help a business establish a social media presence, but Facebook also has games like Farmville, which can impact productivity.
AV&C can be configured to allow the basic access to Facebook, but block access to games and other embedded applications which may contradict company policies.
Encryption
If the traffic from the client to a server is encrypted then the IronPort can’t see the traffic and cannot apply the policies.
There is a solution to this as well. A trusted certificate can be installed on the IronPort, which will be presented to the client during the TLS handshake.
Once the connection is set up, the IronPort will decrypt traffic from the client, inspect it and then re-encrypt the traffic with the destination server’s public key to ensure that the traffic is secured when crossing the Internet.
This method ensures that the clients are following company policy and that their traffic is secure across the Internet.
The IronPort security appliances allow for granular control of web traffic. For example, they give you the flexibility to allow some social media to promote your business but block time-consuming games.
In addition to the flexible control, you can reduce the attack plane and defend against browser-based threats.






