Article How to Implement an IT Security Plan in Wealth Management
By Insight Editor / 1 Jun 2018

The wealth management industry faces major cybersecurity threats, particularly in terms of the loss or exposure of client data, such as personal identifiable information, and illicit transfers and theft of client wealth. However, though shielding against cyber-threats is vital, wealth managers are under increased market pressures that cut profitability and force potential deficiencies in operational spending.
Among these deficiencies is IT security. Many wealth management firms maintain limited and relatively obsolete information security systems. In effect, they’re behind in both current security standards and defensibility against emerging cyber-threats.
Falling to these threats can be fatal. In addition to the high-cost of recovery — involving penalties from the government, compensating clients and building an acceptable IT security system after the fact — is the loss of reputation in the industry and marketplace. Thus, implementing a robust IT security plan in your wealth management firm should be a matter of urgency.
Why Should Wealth Managers Focus on Security?
Poor IT Security is Costly
Though securing your wealth management firm’s information assets is an expensive endeavour, the direct cost of succumbing to cyber-crime is much higher. The total average cost of cyber-crime (for all industries) stood at $11.7 million in 2017 (following a 22.7% rise since 2016).
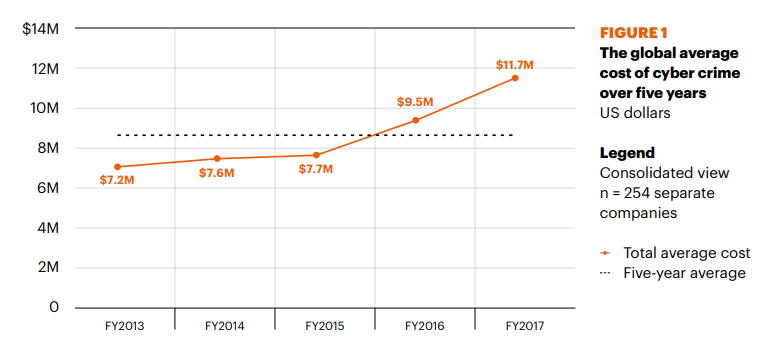
However, the average cost of cyber-crime to the financial services industry is much higher. According to Accenture’s Chris Thompson, “Average annual cost of cyberattacks for financial services firms is [nearly] $20 million.” In effect, the cost of cyber-crime to financial services firms is almost 70% higher than the cost for businesses in general.
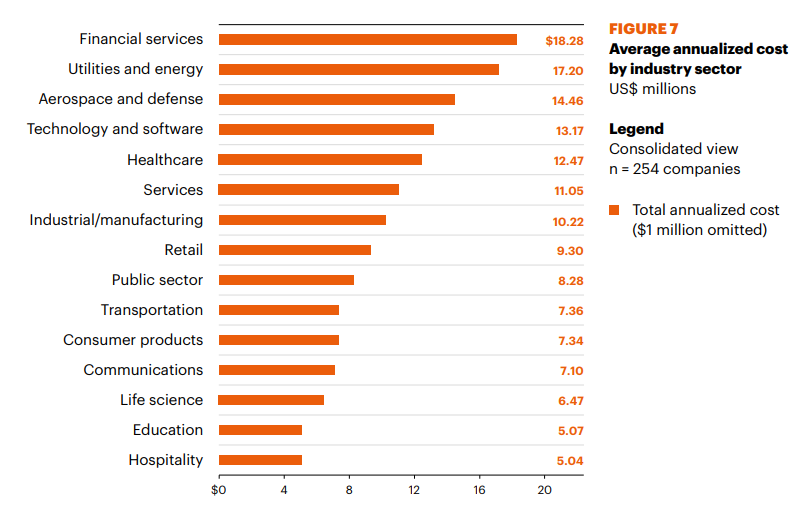
Should your wealth management firm be afflicted by cyber-criminal activity, you’ll be liable for the direct cost of recovering from the attack, along with a series of related costs ranging from penalties to customer compensation. Implementing an IT security plan today will help shield you from these risks and save your bottom line from unanticipated costs.
Your Reputation Matters
Besides the monetary cost, becoming a victim of cyber-crime can be fatal to your reputation in the wealth management industry. You’re already pressured by factors outside of your control such as interest rates, but losing clients because of a bad security record will cut you off from sustainable revenue sources.
This is an acute issue because of the financial services industry’s heavy – and growing – reliance on client data for customization and value-added services. On the other hand, personal information is the costliest area of cyber-criminal activity, rendering client data as your asset, your leading security liability and your costliest area to repair.
However, if your security is suspect or perceived as inadequate, customers will not submit their personal information to your wealth management firm. According to PwC, 85% of consumers in the US said that they “won’t do business with a company if they have concerns about its security practices.” Thus, recovering from cyber-crime does not ensure success; it’s best practice to get ahead of your security risks and shield yourself.
Don’t Forget about Regulations
Inadequate IT security measures could yield government penalties following a breach, and some countries have become proactive and imposed strict compliance requirements.
The banking industry already spends $270 billion (approximately 10% of its operating cost) on aligning with government regulations. However, non-compliance carries the risk of very costly penalties, not just from in your host country, but from abroad as well.
The European Union’s (EU) General Data Protection Regulation (GDPR) is the most notable example of this issue. The GDPR came into force in May of 2018 and requires you to significantly strengthen your data collection, processing and management (specifically for data related to EU citizens.)
It applies to all entities managing EU citizen data, including companies based outside of the EU. The EU imposes a penalty of up to 4% of your global revenue for every violation of the GDPR. You could also be liable to civil legal action due to non-compliance with the GDPR; on the first day of the GDPR, Google and Facebook were struck with lawsuits worth $8.8 billion.
How to Implement a Wealth Management IT Security Plan
Your IT Security Plan is an Ongoing Plan
It’s vital to understand that your IT security plan is an ongoing effort.
The cybersecurity and cyber-crime environments are constantly changing in terms of security threats, standards and tools for shielding against those threats, and your surrounding regulatory environment.
This affects you on at least two fronts:
- First, your wealth management firm must keep abreast of its IT security environment so that you can adjust.
- Second, your technology, training and processes will keep changing, which necessitates continual, long-term investment.
Thus, your IT security plan is not a one-off acquisition, but a permanent element of your operational planning and budgeting.
1. Understand Your Regulatory Environment
First, build a thorough understanding of your regulatory environment. In addition to reviewing the relevant laws and regulations in your jurisdiction (including the EU if you’re collecting and storing EU data), identify your regulatory stakeholders – i.e. federal departments, state and/or provincial bodies, and industry entities to whom your wealth management firm is accountable.
2. Identify Your Assets
Second, identify your assets. This can include hardware, software and third-party services you use throughout your business operations. In general, your assets are a conduit through which cybersecurity threats can occur. Data – including the personal information of your clients – is also an asset in that it’s a cyber-crime target that flows in a number of your other assets, such as applications.
3. Identify Your Threats
Third, properly determine the cyber-threats faced by your wealth management firm. This is vital as it’ll shape the outcome of your security safeguards. In general, your wealth assets and client information are likely to be the main targets for cyber-criminals. Common threats in the wealth management and financial services industry include malware, exploits, social engineering and failures in maintaining controls on access to data and other assets.
You could identify both internal and external threats, in which case you’ll need to view your IT security plan as a holistic project that combines technology and organizational processes designed to mitigate risk. For example, preventing a phishing attack will require both the necessary software safeguards, such as encryption, along witheducation for employees to properly identify and prevent cyber-crime.
4. Identify Your Vulnerabilities
Once you’ve completed an audit of your existing accountabilities, assets and threats, determine your vulnerabilities. Your wealth management firm’s IT security vulnerabilities could manifest in a number of ways. For example, you could have legacy applications that fail to meet current security standards, inadequate data monitoring, and poor end-user awareness and training in managing potential security concerns.
5. Get Organizational Buy-In
Ensure that you have complete organizational buy-in. Your internal stakeholders are essential to bringing an effective IT security plan to fruition. From the executives who must review and approve the program to theinternal end-users who must work with the IT security system, your IT security plan’s success hinges on organizational acceptance in order to work.
6. Prioritize & Secure Your Weakest Link
You might not have the fiscal bandwidth to fill every IT security gap immediately. In this case, you’ll need to identify your greatest vulnerability and prioritize it. This could involve legacy applications in need of replacing or changing how you host data -- for example, moving your data to a trusted cloud-hosting solution.
7. Incorporate an Incident Response System
Though you’ve worked to prevent calamtiy, you’ll still need to develop a set of responses for incidents affecting your IT security system, including the worst-case scenario of a breach. This is where understanding your compliance needs is a must, as different jurisdictions and industry bodies have their own requirements for responding to cyber-attacks. For example, the GDPR requires you to openly notify of a personal data breach within 72 hours of it occurring.
In 2016, EY (Ernst and Young) stated that as many as 35 million cyber-attacks occur on large enterprises and organizations each year. We can comfortably acknowledge that a significant portion – if not most – of these attacks have been levelled at the financial services industry.
Undoubtedly, the cost of cyber-security is very high, but falling victim to cyber-criminal activity will incur permanent damage to your wealth management firm’s reputation. You can begin closing this risk with a well-defined IT security plan under our wealth management IT services.





